With so much of our personal information available online, criminals no longer...


With so much of our personal information available online, criminals no longer...

Cyber resilience refers to the ability to protect electronic data and systems...

A digital signature is a mathematical technique used to validate the...
In today’s digital world, enterprise IT and security professionals are increasingly seeking identity and access management (IAM) services to provide secure and positive customer experiences. We’re...
Rising need for better data security and disaster recovery solutions and growing demand to improve workload performance are some key factors driving global hyper-converged infrastructure market...
The sheer number of tasks we do online grows every year as we create and discover new opportunities to digitize our world. This is true within the workplace as well, but as we find more processes...

Converged IAM (Identity and Access Management) unifies disparate physical and logical access control systems to create a singular trusted identity and credential to match rights and access them across the enterprise. Converged IAM can't exist without network...
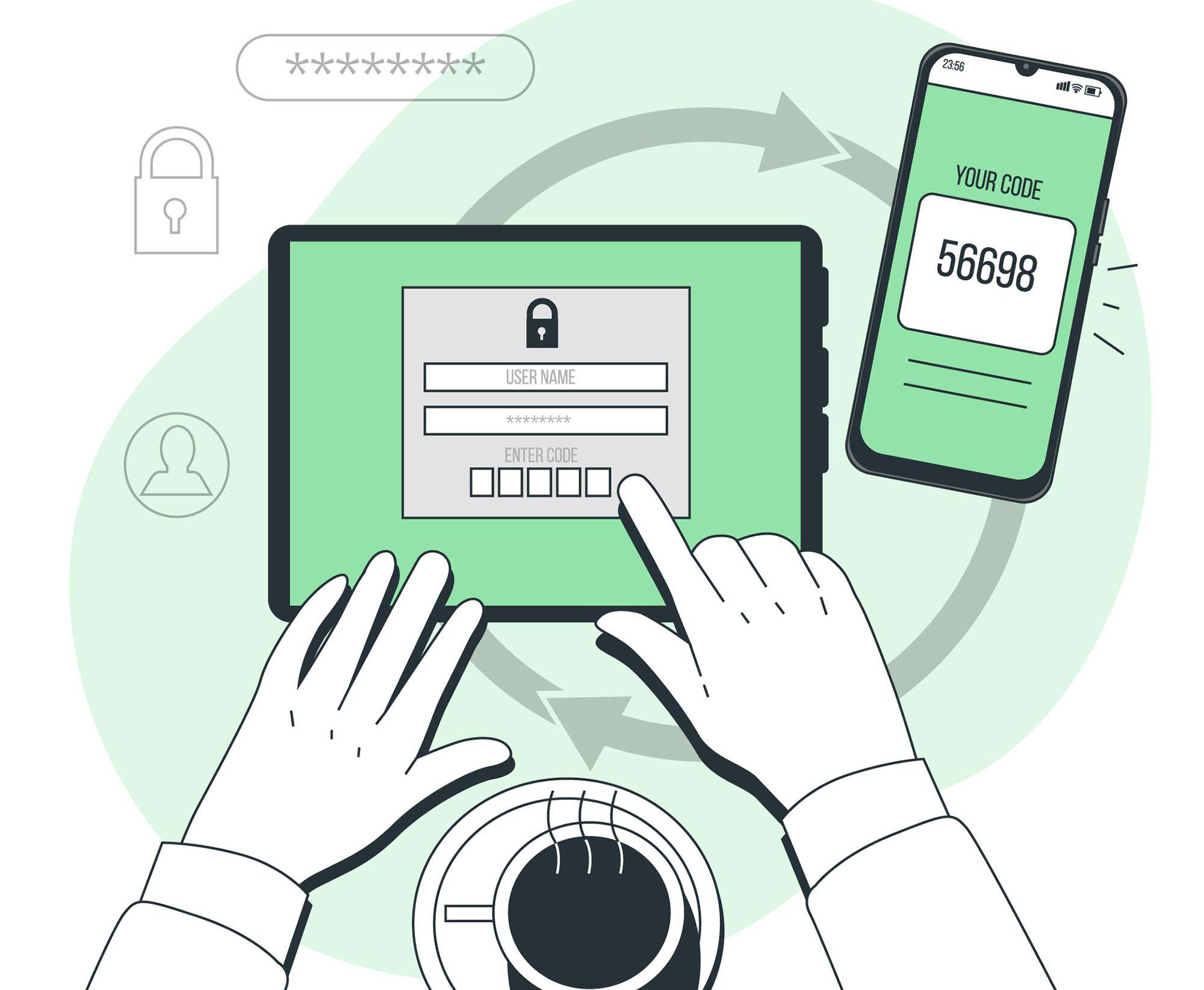
Multifactor authentication (MFA) is a security technology that requires multiple methods of authentication from independent categories of credentials to verify a user's identity for a login or other transaction. Multifactor authentication combines two or more...

The attack surface is the number of all possible points, or attack vectors, where an unauthorized user can access a system and extract data. The smaller the attack surface, the easier it is to protect. Organizations must constantly monitor their attack...

People everywhere continue to increase the amount of time they spend on their electronics. A higher usage of technology in comparison to the past is not necessarily a bad thing; however, it seems that using technology is becoming the general population’s go-to thing...