Cyber threats are real—and more common than you think. The word “threat” is...


Cyber threats are real—and more common than you think. The word “threat” is...

Nowadays, Chief Information Officer are focusing on business outcomes,...

The company of today, both private and public, face a daunting variety of...
Passwords are designed to give you access to an online world while companies protecting your information. However, password security can lead to attacks. This first point of cybersecurity is...
Cyber security has always been an unsought goods like, insurance, which is useful only when something bad happens. And It’s always been challenging for security leaders to communicate the value of...
Multifactor authentication (MFA) is a security technology that requires multiple methods of authentication from independent categories of credentials to verify a user's identity for a login or other...

The company of today, both private and public, face a daunting variety of threats to cybersecurity. A cyber attack can threaten the very existence of an organization. And even the jobs of some of its C-suite officers. But the response doesn't rest solely on a building...

Passwords are designed to give you access to an online world while companies protecting your information. However, password security can lead to attacks. This first point of cybersecurity is becoming a weak spot that can involve dire consequences if unaddressed for...
Cyber security has always been an unsought goods like, insurance, which is useful only when something bad happens. And It’s always been challenging for security leaders to communicate the value of cybersecurity investments to board and peers. Furthermore, everyone in...
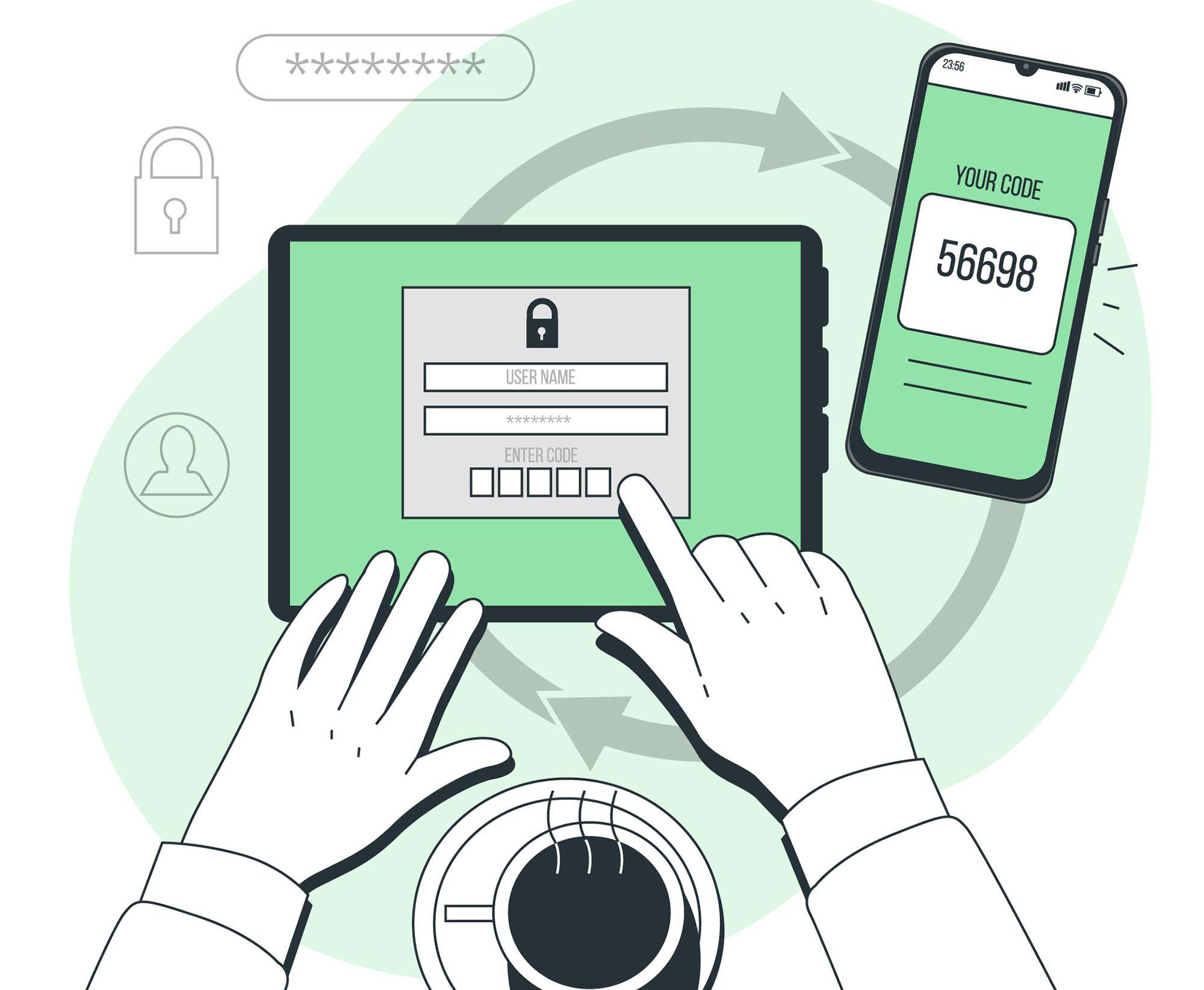
Multifactor authentication (MFA) is a security technology that requires multiple methods of authentication from independent categories of credentials to verify a user's identity for a login or other transaction. Multifactor authentication combines two or more...