
by Rebeca | Mar 25, 2024 | soffid, trends
The shift towards cloud services is a discernible trend among today’s organizations, driven by the undeniable benefits of cost savings, improved availability, and enhanced flexibility. The transition to cloud computing promises a significant reduction in Total Cost of Ownership (TCO) and offers an agility that traditional on-premise solutions struggle to match. However, this increasing reliance on cloud providers introduces a risk often underestimated by many: the management of authentication credentials.
The Growing Challenge of Password Management
As organizations utilize a broader array of cloud services, the proliferation of passwords, One-Time Password (OTP) devices, and tokens begins to exceed the management capabilities of IT staff. This complexity harbors several risks worth noting:
- Password Overload: The practice of using unique passwords for each system, while secure in theory, leads to two significant issues. Users often resort to reusing passwords across platforms, posing a security risk if one provider’s database is compromised. Moreover, each additional cloud service increases the vulnerability to attacks, including phishing and exploits targeting specific cloud platforms.
- Browser-based Password Managers: While convenient, password managers integrated into web browsers double the risk. They become prime targets for traditional cyber threats, such as trojan horse attacks, due to their extensive attack surface.
Towards a Password-less Future
The consensus among cybersecurity experts is clear: the future lies in moving beyond passwords as the sole method of authentication. However, this transition introduces its own challenges, notably the proliferation of authentication tokens, which merely substitutes one problem for another.
To address this, the creation of an enterprise identity service is imperative. Such a service would facilitate user authentication across various applications and protocols, not limited to modern standards like SAML and OAuth but also encompassing legacy systems.
Hard Authentication Tokens and Behavioral Analysis
Implementing hard authentication tokens is a pivotal next step. Solutions like the Soffid Push Authenticator offer a secure and user-friendly option, though the specific needs of an organization may necessitate alternative methods, such as SMS, email, or TOTP tokens. The flexibility to adapt authentication methods to different scenarios is crucial.
Moreover, integrating network intelligence and behavior analysis enhances security by reducing the interaction required from the user, thereby minimizing the attack surface accessible to hackers.
The Benefits of Comprehensive Identity Providers
The deployment of enterprise identity providers yields immediate and tangible benefits:
- Increased Productivity: Simplifying the login process reduces the time spent on password recovery efforts.
- Enhanced Security: Cloud providers will not have access to user passwords, and the risk of phishing significantly decreases.
- Improved User Satisfaction: Employees benefit from a more streamlined and secure access management system.
In conclusion, as organizations continue to embrace cloud services, the need for robust, flexible, and secure identity and access management solutions becomes ever more critical. By adopting advanced authentication technologies and practices, companies can protect their digital assets while ensuring a seamless and productive user experience. Soffid is at the forefront of this transformation, providing the tools and expertise needed to navigate the complexities of identity management in the cloud era.

by Rebeca | Mar 19, 2024 | soffid, trends
In the modern enterprise, the adoption of DevOps practices is more than a mere trend; it’s an evolution in how organizations approach software development and IT operations. This innovative methodology has proven to unify teams and processes, offering substantial benefits across the board. However, integrating development and IT operations presents unique challenges, particularly in the realm of security.
Historically, friction between IT operation teams and development teams has been commonplace, primarily due to differing security cultures. DevOps aims to eliminate this friction by harmonizing practices and goals. Yet, it’s important to recognize that while DevOps can reduce visible conflicts, it doesn’t inherently solve underlying security issues—often, these issues are merely obscured until they surface as significant problems.
One area where this disparity becomes evident is in the utilization of Privileged Access Management (PAM) solutions. IT operation departments have traditionally employed PAM to some extent, safeguarding access to critical assets like operating systems, network devices, and databases. Conversely, development departments have lagged in PAM adoption. The reason is straightforward: PAM solutions were originally conceived with IT operations in mind, rendering them less applicable or flexible enough for the development lifecycle.
DevOps, however, introduces its own set of critical assets, notably containers and secrets, which necessitate a new approach to privileged access. The DevOps workflow allows developers to use familiar tools for container configuration, yet access to production containers for troubleshooting or updates poses a significant security risk.
To mitigate these risks, leading-edge PAM solutions offer mechanisms for safe container access, such as shell-like sessions that are fully recorded, with every keystroke and file transfer monitored. This capability enables the detection of risky behavior or unauthorized actions, thus maintaining the integrity of the production environment.
Moreover, the management of secrets—such as database passwords—requires a PAM solution capable of securely updating credentials in real-time, often within Kubernetes secrets, to ensure both security and operational continuity.
At Soffid, our expertise in navigating these complexities is unparalleled. With both PAM and Identity and Access Management (IAM) engines integrated into our Converged Identity Platform, we are uniquely positioned to address the specific needs of DevOps environments. Our solution not only accommodates the dynamic nature of microcontainer-based operations but does so without sacrificing the agility and security that are critical to DevOps success.
In essence, the journey towards integrating DevOps into an organization’s DNA is fraught with potential security pitfalls. However, with Soffid’s innovative approach to PAM and IAM, organizations can embrace DevOps with confidence, ensuring that their development and operational practices are secure, efficient, and, above all, unified.

by Rebeca | Mar 12, 2024 | soffid, trends
Customer Identity Management is increasingly gaining more relevance. The complexity of identification and authentication protocols is rising due to different factors, with the most relevant being:
Some standards are very new or still in a draft version. For instance, the OpenID logout protocol specification was approved only 16 months ago.
Legacy protocols are hard to implement. In fact, the NSA has encouraged all organizations not to attempt to implement SAML by themselves, as a poor implementation can lead to multiple security vulnerabilities.
Security vulnerabilities have a dramatic impact on organizations. In our case, a security bug in a CIAM authentication module can lead to high levels of fraud, putting the whole organization at risk.
On the other hand, despite having a secure environment being a must, it can be a barrier to enrolling new customers. The process to identify and harden user identification should be progressive: let the user access anonymously, identify them only when it is really needed. Later, suggest to the end user to enroll in a hard authentication token. The customer must have an easy-to-go path, but at the same time, they must feel comfortable and secure.
However, keep in mind that once the hard authentication token is granted, always asking for it can be annoying, and we don’t want to bother our customers. The solution is to have a smart engine able to assign a risk level to each transaction and ask for the second authentication factor when the risk level is above one threshold. For instance, if the user is connecting from the same origin country, using the same device, we probably will not ask for the second authentication factor, but if they are connecting from a new device from a foreign country, the second authentication factor is really needed.
For any SaaS provider, focusing on these aspects can be cumbersome and prone to errors. That’s the reason why CIAM platforms like Soffid IDaaS are gaining a lot of interest. Using these tools, organizations can focus on the relevant aspects:
- Defining the customer journey
- Defining the authentication levels required at each step
- Configuring the CIAM tool to manage all authentication problems
- Customizing the CIAM tool to look and feel like the organization’s customer platform.
In turn, the CIAM tool takes responsibility for some critical aspects:
- Registering end users
- Allowing the user to reset their passwords
- Enrolling a second authentication factor
- Asking for a second authentication factor when needed.
In conclusion, CIAM is a specialized version of traditional access management platforms, but its challenges and risks are unique. A CIAM project cannot be addressed as a traditional access management project. Additionally, based on our experience at Soffid, the team profile is also different. In access management projects, the main actor is the IT managers’ team, but in CIAM projects, we need to engage the IT team, business team, and also development teams.
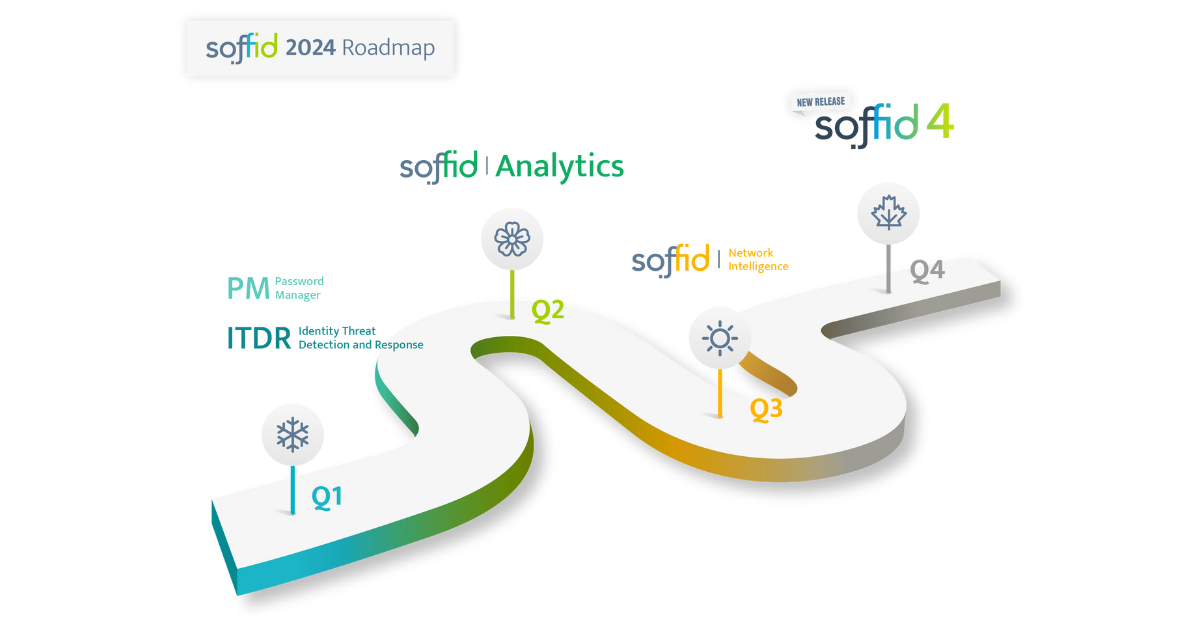
by Rebeca | Mar 7, 2024 | soffid
We are thrilled to announce the exciting new features and enhancements that are coming to Soffid in 2024. As part of our ongoing commitment to providing a secure and reliable platform, we have been diligently working to deliver innovative solutions that address the evolving needs of our customers.
One of our top priorities for 2024 is achieving the Common Criteria certification, a testament to our dedication to quality and security. This certification will provide our customers with added confidence in the reliability and integrity of our platform.
In addition to pursuing certification, we are focused on enhancing our security offerings to help organizations better protect their assets. With more than 60% of ransomware and targeted attacks originating from compromised accounts, we are introducing a set of services designed to make it extremely difficult for attackers to gain unauthorized access.
To combat this threat, we are promoting the use of Soffid Authenticator, a mature and user-friendly tool that eliminates the reliance on passwords as the primary method of authentication. Coupled with our network intelligence feeds, which detect suspicious activity and connections from different countries, organizations can significantly reduce the risk of account compromise.
In terms of user experience, we are making significant improvements to our user interface, including better integration with mobile platforms and easier configuration of custom dashboards. Additionally, our BPM editor will feature a new graphical editor, simplifying the review of identity lifecycle processes.
For privileged account management, we are streamlining integration with container-based platforms like Kubernetes and Docker Compose, eliminating the need for SSH jump servers and enhancing overall security.
Furthermore, we are simplifying the enrollment process for strong authentication methods, making it easier for administrators and end-users to adopt advanced security measures seamlessly.
Looking ahead, we are excited to announce two major advancements in our long-term research efforts. First, we are exploring the use of face recognition as a dynamic risk evaluation criterion, offering enhanced security for trusted systems. Additionally, we are leveraging AI technology to enhance the user interface, setting new standards for security, precision, and confidentiality.
Overall, our roadmap for 2024 reflects our commitment to innovation and our dedication to providing our customers with the tools and solutions they need to succeed in today’s rapidly evolving threat landscape. We look forward to sharing more updates and insights with you in the coming months. Stay tuned for more exciting developments from Soffid!

by Rebeca | Feb 27, 2024 | trends
The National Security Agency (NSA) of the United States has recently released a comprehensive document shedding light on the intricate landscape and challenges of Identity and Access Management (IAM) solutions. The document, available at https://media.defense.gov/2023/Oct/04/2003313510/-1/-1/0/ESF%20CTR%20IAM%20MFA%20SSO%20CHALLENGES.PDF, is aimed at IAM developers and vendors, offering valuable insights and recommendations for addressing evolving threats in the digital realm.
According to the NSA report, malicious actors are increasingly exploiting vulnerabilities in identity and access management systems to impersonate legitimate entities, influence operations, and exploit sensitive information. This underscores the critical importance of implementing robust IAM solutions capable of mitigating such risks effectively.
The challenges outlined in the document are relevant to organizations of all sizes. While smaller companies often face budgetary constraints and resource limitations, larger enterprises contend with sophisticated adversaries and complex infrastructures. However, irrespective of size, the deployment of Multi-Factor Authentication (MFA) and Single Sign-On (SSO) solutions is imperative for enhancing security posture and ensuring operational reliability.
One of the key challenges highlighted in the report is the selection of an appropriate MFA solution. Organizations must carefully evaluate technical options based on deployment ease, end-user experience, and cost-effectiveness. Moreover, comparing MFA products from different vendors can be daunting due to the diverse range of technologies and features available.

A crucial aspect emphasized by the NSA is the integration of MFA enrollment into the identity provisioning process. This holistic approach ensures that MFA authentication lifecycle management is seamlessly integrated, thereby enhancing overall security and trust in MFA usage.
Centralizing authentication and SSO functions within a dedicated platform such as Soffid Identity Provider offers numerous benefits, including streamlined policy management and enhanced security controls. However, it also necessitates robust protection measures to safeguard the identity provider from potential threats. Soffid’s attainment of the Common Criteria Certification underscores its commitment to delivering top-tier security standards.
Furthermore, the NSA advocates for the adoption of identity provisioning standards like SCIM (System for Cross-domain Identity Management) to facilitate seamless integration and interoperability across diverse systems.
In terms of SSO protocols, the NSA acknowledges the superiority of OpenID Connect over traditional protocols like SAML (Security Assertion Markup Language), citing its enhanced security and simplified design.
Lastly, emerging technologies such as the Shared Signals Framework, endorsed by the OpenID consortium, hold promise for bolstering real-time threat response capabilities by enabling immediate session termination in the event of a compromised account. While Soffid already supports the Shared Signals Framework, ongoing developments in this area are anticipated to further enhance security and efficiency.
Overall, the NSA’s comprehensive report underscores the evolving nature of IAM challenges and the critical role of innovative solutions in mitigating emerging threats. By staying abreast of industry trends and leveraging advanced technologies, organizations can strengthen their security posture and safeguard critical assets in an increasingly complex digital landscape.







